I spent some time in late December thinking about writing a recap of cyber trends in 2012. However, in the midst of the holidays, I realized that I have so many other associates, colleagues and friends who had already published their thoughts, so the topic had already been covered rather extensively.
Late last year we recorded a podcast where I outlined some cyber trends and themes for the coming year; it’s worth a listen if only to get a perspective through my personal rose-colored glasses.
Anyhow, I still wanted to add my two cents to the mix, so I decided to approach the topic a little differently. Rather than offer up some links that any reader can easily Google, I thought I would post links to some of the most relevant texts I read in 2012, some videos, as well as a statement regarding the general direction of both the infosec industry and the threats being faced.
To start with, here is some reading material:
1) 21st Century Chinese Cyberwarfare
Despite some questionable work done (or ignored) by the editor; this is an informative text as it relates to the future of technical espionage in the coming years. Whether you are in federal or commercial sectors, the information within applies. And whether you realize it or not, your threat model has changed underneath your feet.
2) National Intelligence Council’s (NIC Global) Trends Report
While this piece is not directly related to cyber, it is worth reviewing because our means of communication and commerce are directly tied to our global telecomm infrastructure. Download the free PDF or Google for the shorter “Le Menu” version.
3) Securing the Virtual Environment: How to Defend the Enterprise Against Attack
This is the go-to book for understanding the risks, threats and mitigations within virtual environments and the cloud realms.
4) Global Warrior: Averting WWIII
If you are involved in technical I/O and want to know how your work impacts the supply chain and/or are curious about how I/O is felt by boots on the ground, H. John Poole’s book is a worth read and readily complements 21st Century Chinese Cyberwarfare.
5) Kill Decision
Lethal Autonomous Drones (UAS), hacking, forensics, espionage, intelligence… Irarely indulge in fiction, however this book is an exception. The best part of Suarez as an author is that he has a deep technical background, and he has access to the right people so much so that his books are seemingly prescient (Read Daemon and Freedom ) and technically relevant.
The general theme I’m seeing is an increased dependence upon niche security services from specialty providers as well as an increase in the use of “thinking opponent tools” such as honeytokens/pots/networks –and security vendors will be moving towards “intelligence based products” that help address the who/what/where and why of an attacker.
The age old investigative question “Cui Bono” (to whose benefit?) is finally being brought into security incident investigations and this is a natural progression.
Lastly, as JoeSixPack continues to read about breaches and incidents in The Wall Street Journal it’s safe to say infosec and hacking terms will continue to invade the cafeteria lexicon. Good, bad or indifferent, security awareness is rising. Whether that actually helps fix anything is a wholly different story…
Take a gander at the 2012 Breach-Timeline and here is a snapshot:
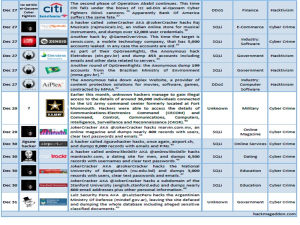
From a significant increase in numerous state sponsored threats, to the various flavors of hacktivism and outright cybercrime (think ID theft) – the average organization from SMBs to Fortune 100 will continue spiraling down the infosec rabbit-hole. So, based on the last five days of 2012, I would be willing to say that it’s safe bet 2013 is going to be even more action packed!
Lastly, If anyone is going to be at the Spooks and Suits event in Arlington, B-SidesSF or RSAC reach out to me and we can get together in person.
Good luck and stay safe!
COMMENTS